Executables signed with a reputable code signing certificate get better SmartScreen treatment. A signed executable proves that it hasn’t been tampered with by anyone who does not have the signature key.
To sign your code, you’ll need to generate a private key and public certificate. The public certificate will need to be signed by a certificate provider to validate your organization.
This process uses OpenSSL and Windows.
Generate the private key and certificate signing request using the following command.
openssl req -utf8 -nodes -newkey rsa:4096 -keyout NAME.key -out NAME.csr
Enter your details. Submit the contents of the name.csr file to your certificate provider (e.g. Xolphin), ordering a code signing certificate. Organization Validation is the cheapest option, goes around EUR 100 for a year’s validity. Go through the validation process.
The name.key file contains your private key. Your certificate provider will never see this file. Keep it safe.
When ready, you’ll get a collection link in the mail. This will download a file, which might be called CollectCCC, user.crt, or something else, depending on your provider. This file contains your public certificate, signed by the certificate provider. Rename the collected certificate to name.p7s or name.crt, depending on the file type. If you got a zip file instead, and it contains a name.crt file, use that one.
Install the public p7s or crt file to your Personal certificate store. Using the Windows certificate manager. Right click your certificate and export it to the base64 format. Save as name.cer. Delete the public certificate from the certificate manager, since it’s useless.
Issue the following command to combine the signed name.cer certificate with your private key name.key.
openssl pkcs12 -export -out NAME.pfx -inkey NAME.key -in NAME.cer
This creates a name.pfx file, which you can install directly in the Personal certificate store on the computer where you want to sign your executables. You can use the Windows certificate manager to add a friendly name to the certificate.
To sign an executable, run signtool, as follows. Set the timestamp provider appropriately. Both exe as well as dll can be signed. The certificate fingerprint can be found by opening the certificate’s details panel.
"C:\Program Files\Microsoft SDKs\Windows\v6.0A\Bin\signtool.exe" sign /sha1 YOUR_CERTIFICATE_FINGERPRINT /t http://timestamp.comodoca.com/authenticode "helloworld.exe"
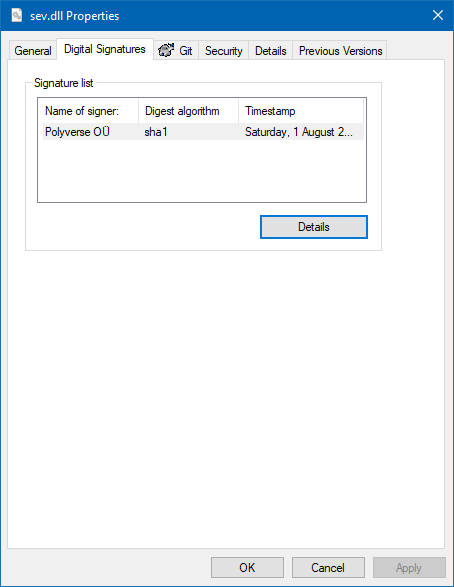
Right click your executable, and check Properties, to verify.




Recent Comments